Password Meters Suck
It is false economy. And worse than not having it at all. It condones poor habits and impede progress. No wonder the top 10 passwords are still:
123456
password
12345
12345678
qwerty
123456789
1234
baseball
dragon
football
Most password meters are junk. Here is Drupal's:
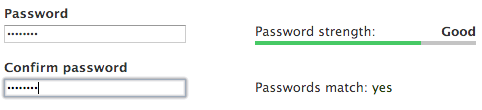
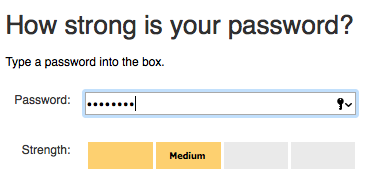
And Microsoft's:
What was my password? It was the second most common password in the world, just with a capital letter P:
Password
Look how long it takes me on an average desktop PC to crack that (without assuming anything about the password):
dc647eb65e6711e155375218212b3964:Password
Status.........: Cracked
Started: Tue Sep 15 11:31:00 2015
Stopped: Tue Sep 15 11:31:03 2015
Duration: 3 seconds. And those two meters consider it Good and Medium, respectively? Lets make it harder. Lets use the following password:
P@55w0rd
Surely that has to be hard to crack. Lets see:
Time to crack:
37e4392dad1ad3d86680a8c6b06ede92:P@55w0rd
Status.........: Cracked
Started: Tue Sep 15 11:35:41 2015
Stopped: Tue Sep 15 11:35:43 2015
2 seconds...
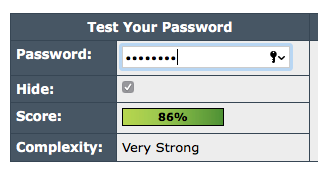
Lets try to find a password checker that is stronger... Lets use this password:
00Andersen19
Intel's password strength meter thinks this is OK:

Lets see how long to crack:
f25c5ff80bf7e901950ba3ba0284b584:00Andersen19
Status.........: Cracked
Started: Tue Sep 15 11:52:28 2015
Stopped: Tue Sep 15 11:52:33 2015
5 seconds... Am I cheating? No. I simply exploited the fact that most password meters do not consider the state of mind and approach taken by crackers. Crackers do start with brute force. Here is what I would typically do to attack your password (assuming I have the hash handy, and assuming I know nothing of the victim) - in order, stopping once I cracked it:
- Run the hash through publicly accessible common password lists (this is how I cracked all the above passwords)
- Brute force for all 6 character combinations (symbols, digits, lower and uppercase letters). It takes 7 minutes to complete and will find ANY 6 character password.
- Run the hash through english wordlists
- Run the hash through wordlists mangled with letters and symbols (postfix etc)
- Start running through various other rules and combinations such as l33t
- Run through combined words - i.e. concatenate multiple english words
- Brute force for all 7 character combinations excluding special characters. It takes about 30 minutes.
- Brute force for all 8 character combinations excluding special characters and lower case only. It takes about 30 minutes.
- Continue with various rules and patterns and potentially try other language dictionaries.
- If I really feel like it, I can run all possible 8 character combinations (symbols, digits, lower and uppercase letters) in 44 days on my old rig. A new rig will cut that down to days.
My issue with password checkers is that they do not provide accurate feedback to users. They think their passwords are secure, while in fact they are not. The only password that is really secure (for now) is one that has sufficient entropy that it is unlikely anyone else has ever used it before - meaning it cannot be looked up in any dictionary or wordlist or common password list. That includes Wikipedia. An example:
From "My arm is hurting my leg, because I lie too much"
we can make a password:
mAiHmL,b1lTM
That password surely should be unique as it is long enough, has sufficient entropy from its character classes, and is unique in that it is a contraction from a random nonsense sentence. Alternatively, generate a random password of length 10 or more and use a password manager - as these will not be memorable. Also, never share passwords between sites you care about.
The only password checker I found that is any good, is Kaspersky's.
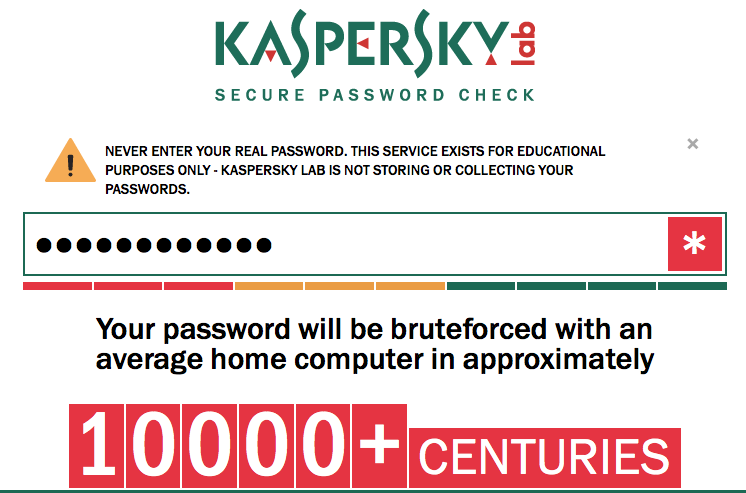
But as always, security is relative. Dropping the last M from that password, a desktop computer will take 8652 centuries (according to Kaspersky), but only 3 months on the world's fastest supercomputer. For highly secure systems it is plausible that someone can and will crack it. It all depends on how valuable the information is you are trying to protect, including ALL locations where this password is used.
I would still be cautious - Kaspersky thinks the following password:
0%,d9Wa~
will take 6 centuries on a desktop PC to crack:
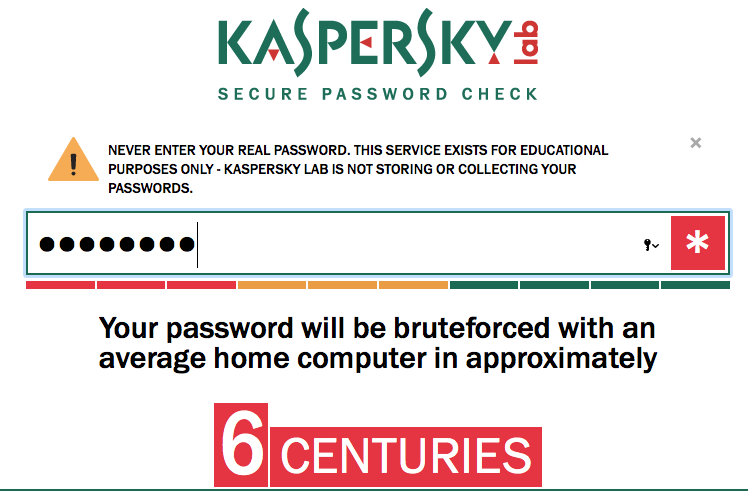
I disagree. I can crack any 8 character password in 30 days on my desktop PC. So my recommendation is, whatever duration it gives you, add at least two characters to ensure adequate security.
On a side note, the Intel password checker uses the same logic than many other checkers. Here is an excerpt of their JavaScript code:
var lowercase_bits = uppercase_bits = 26;
var digit_bits = 10;
var special_bits = 32; //potentially
var entropy = Math.pow(lowercase_bits, lowercase_chars) * Math.pow(uppercase_bits, uppercase_chars) * Math.pow(digit_bits, digit_chars) * Math.pow(special_bits, special_chars);
var entropy = entropy / 2;
var _std_comp_power = 2 * Math.pow(2, 33);
var hours = entropy / _std_comp_power;
My issue with above is that for a truly random password, it is not right to calculate the password strength like that. According to their algorithm, the password
52c104.M
will take 0.13 hours to crack. Whereas the password
,#.5cM$*
will take 13 hours to crack. In my mind, even though the first one's entropy is lower (due to its use of more "lower entropy digits" as opposed to "higher entropy symbols" would not alter how long it takes me to crack it. I cannot apply a selective mask without knowing something about the topology of the password, and since both passwords contain one or more of each character class, I cannot leave one out. Best I can do is perform a brute force of all character classes, which will take on average, exactly the same length of time for both passwords regardless of entropy.