Be Wary of Partial Truths From Commercial Bias
I recently listened to this BlackBerry sponsored summit from 2016 whereby the security person explained how to hack a wireless network through an IoT based kettle. Most of the content is fine and accurate, however one thing did tick me off as it is simply untrue and feels like they said it to promote their own security software. Listen to the Youtube video below, at time 13:24.
He claims that no forensics team in the world will be able to determine how the network was compromised. But that is not entirely true. Seeing that he was targeting an office network, it is reasonable to expect the office may have non residential grade equipment, like Ubiquiti's line of networking equipment. To detect the entry point - i.e. the rogue WiFi access point that was used, the Ubiquiti line of products (and many other enterprise grade equipment) will clearly detect and log the presence of such a rogue access point, as per below, when I tried to perform a similar attack:
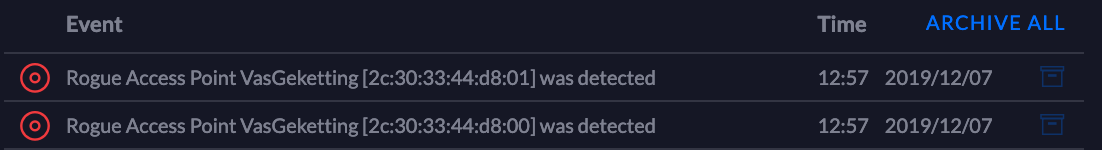
Granted, detecting that the kettle was attacked might be slightly harder. The interaction with the kettle was done entirely over the rogue access point, however it might be possible that the de-authorization requests would have been picked up and logged.
The main issue I have is that he makes it sound like they are the only company that can help protect you against these kind of attacks, which is not true. They are one of many.